Control - The Falsest Security
Control - The Falsest Security
Blog Article
If you are like most online company owner that are using a wireless network, you are most likely unaware of the possible risks to both your company and the security of you and your clients data. In this short article, I'm going to discuss 4 various risks that you must be mindful of when it comes to running a company over a cordless network.
The key is security, and it is essential for having a website that you do not have to worry about. I can not inform you how lots of scary stories I have heard from an unsecure website not being tended to appropriately. Outdated plugins/themes, etc well, that is simply a reproducing ground for potential malware.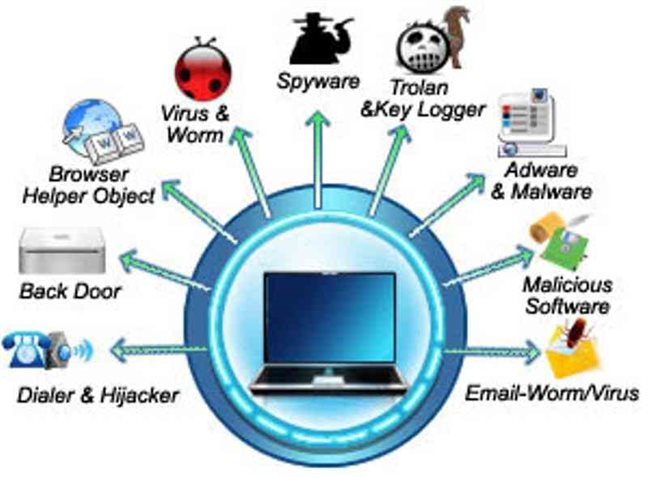
Current research has actually shown obesity is not a failure of character or self-control. Obesity grows from your biological drive to eat. It becomes part of your nature as a private, as a human being, and it's likewise part of the nature of our modern world.
Ensure they utilize strong passwords: A hacker can break a 6 letter all lower case password in less than 6 minutes. They should Cybersecurity Threats utilize passwords with 8 or more characters that include upper and lower case, numbers and letters and special characters.
Be careful of online fraudsters. I understand a guy in Barbados who works for a prominent global organization and is abusing his authority to send me rip-off emails apparently from the FBI. I pity him because of his jealousy of my success, however that goes to show you the calibre of individuals dealing in cybercrime. They're much more advanced than the dodgy, antisocial geeks Hollywood likes to make us consider them as. When it pertains to online fraud, avoidance is the only way. Do not reply, that simply makes them smart about determining your behaviour, unless you want them to consider you as a particular type. XD As a rule of thumb, erase any mail you don't expect. Do not even preview it. That simply fires up your temptation. Simply delete it after you have actually marked it in your inbox as phishing cybersecurity threats scam.
Whatever software you are using (Microsoft Office, Windows Server, etc), you should always keep up to date on the most current service spots. Service spots are merely corrections or additions to software application which are launched after the product has been put on the market. Again, this is easy to do, and it can even be automated, however if it is refrained from doing, it can cause security and other issues. Do not delay this easy task.
Lot of times you get out of the habit of writing to your blog site. Because your readers will drop off losing interest, this is a substantial issue. It will take quite a bit of work to get those readers back.
Needless to say, the real risk with these and other wireless network risks is that the danger to your bottom line is in risk. While some hackers only do what they do to see if they can do it, or to be a just annoyance, thieves that get involved in wireless risks are not of the harmless variety. They can cost you plenty.